This is a journey to a useless but funny hacking.
Introduction
Take a simple iot device and let's try to reverse engineering it and modify some data.
Here is our target:

A simple phone (that actually is broken and does not work anymore) that displays some basic informations such as a logo on boot, dials messages, contacts etc.
Now let's say the main goal is to change the logo at boot I know this is uselless but this could be funny
Case opening
Okay so let's open this thing and see what is under the hood.

Bingo I already found what I wanted the flash memory !
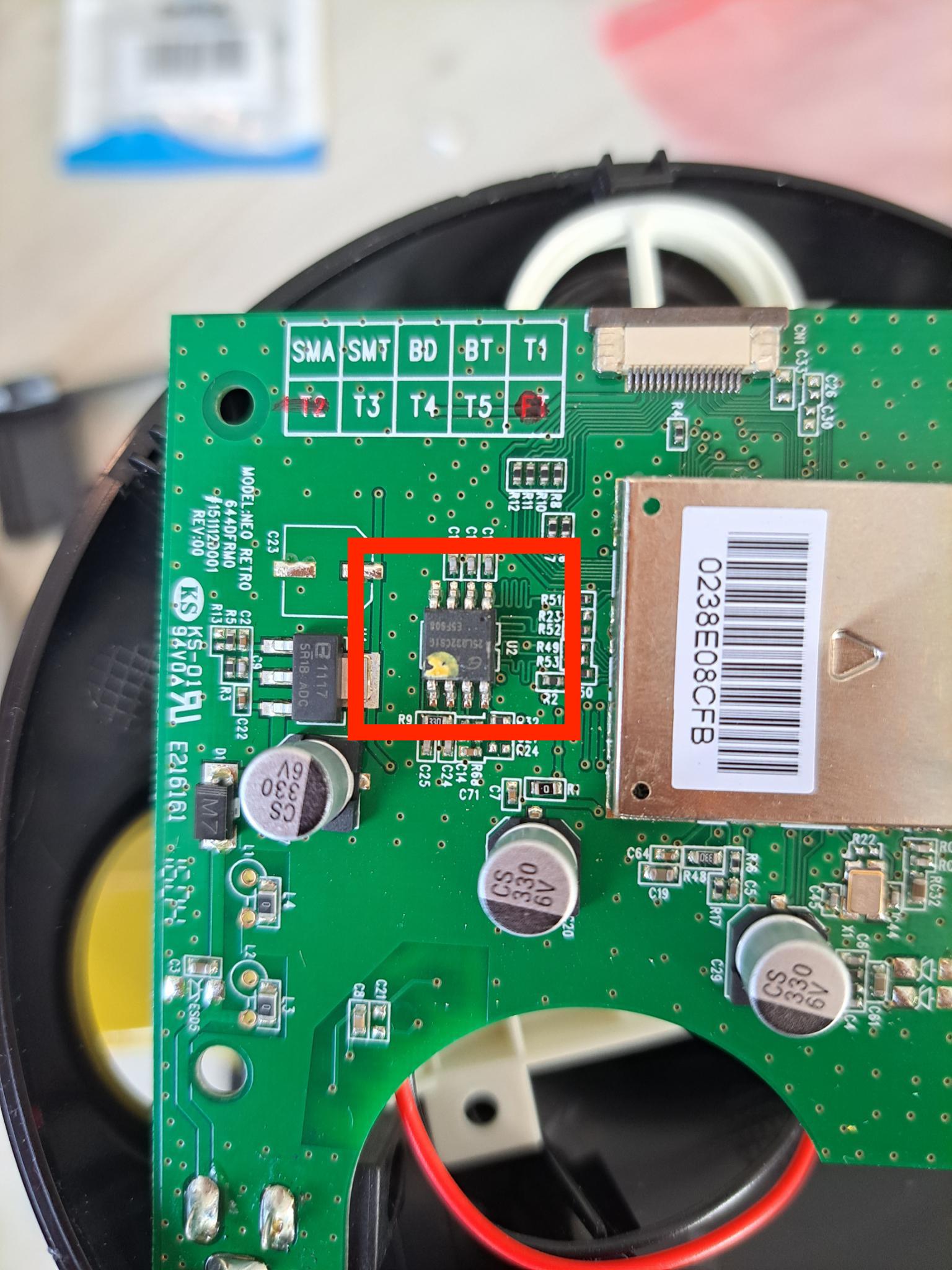
Why do I want this componant espacially ? Because it could contains the firmware of the device and edit it could allow us to put the data I want such as a new logo !
By the way here is the normal logo at boot
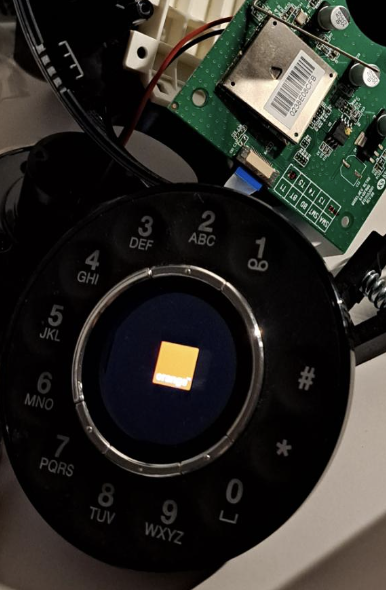
Yes I work there so...
Dumping the flash
There are multiple ways/devices/tools to dump a flash but for this stuff let's use a ch341a spi flash programmer and a chip clip to do so.
The software I use is flashrom
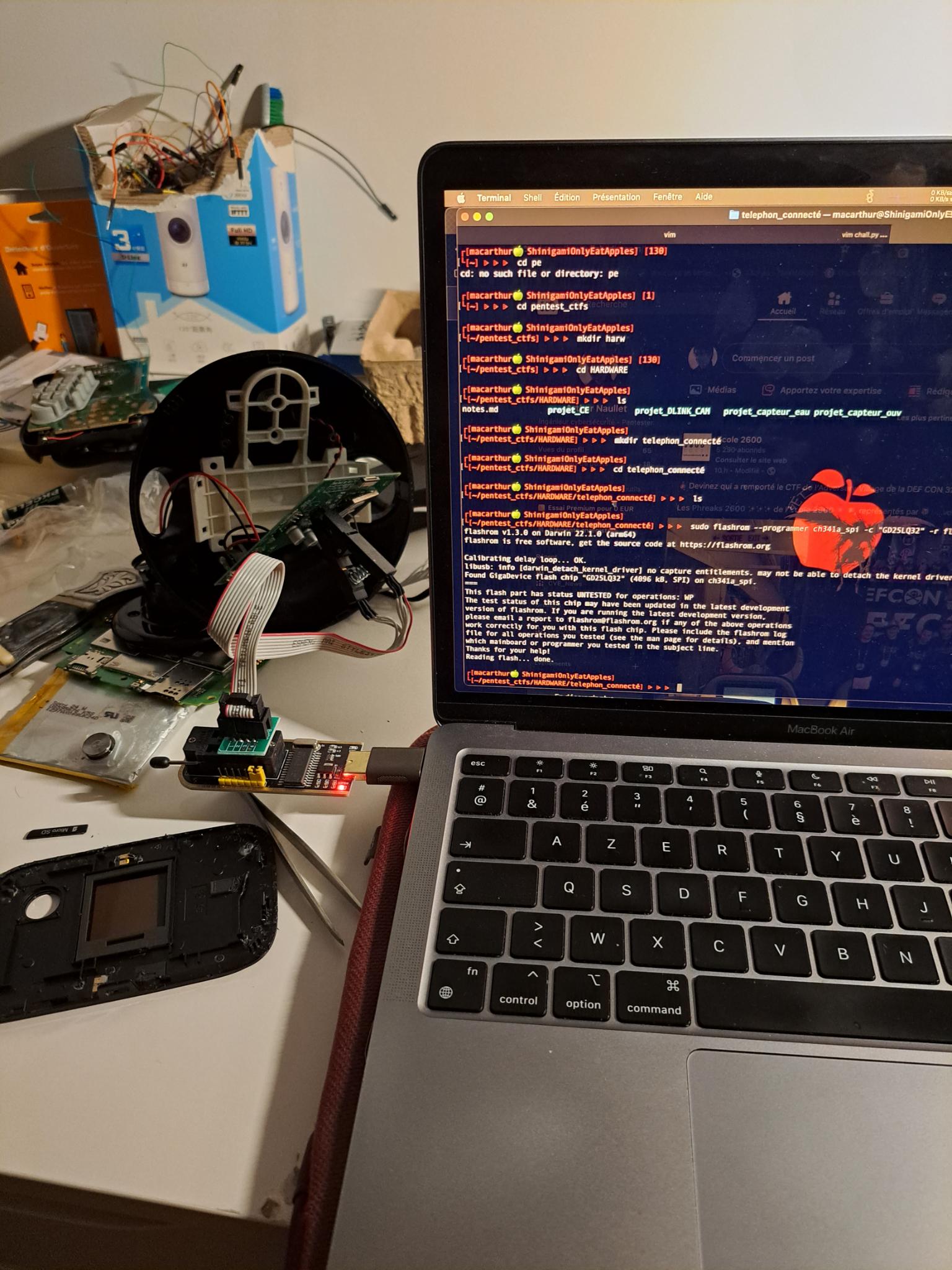
the software first will try to recognize the chip manufacturer and model, once verified, it will dump whole flash data so I can analyse it offline.
Here are our target.
Analyse the flash
The first thing I want to do in these cases it is to understand the structure of the dump, for example, most of the time, I will be able to find a compressed filesystem and may be access somethings that is close to a Linux FS
So let's try
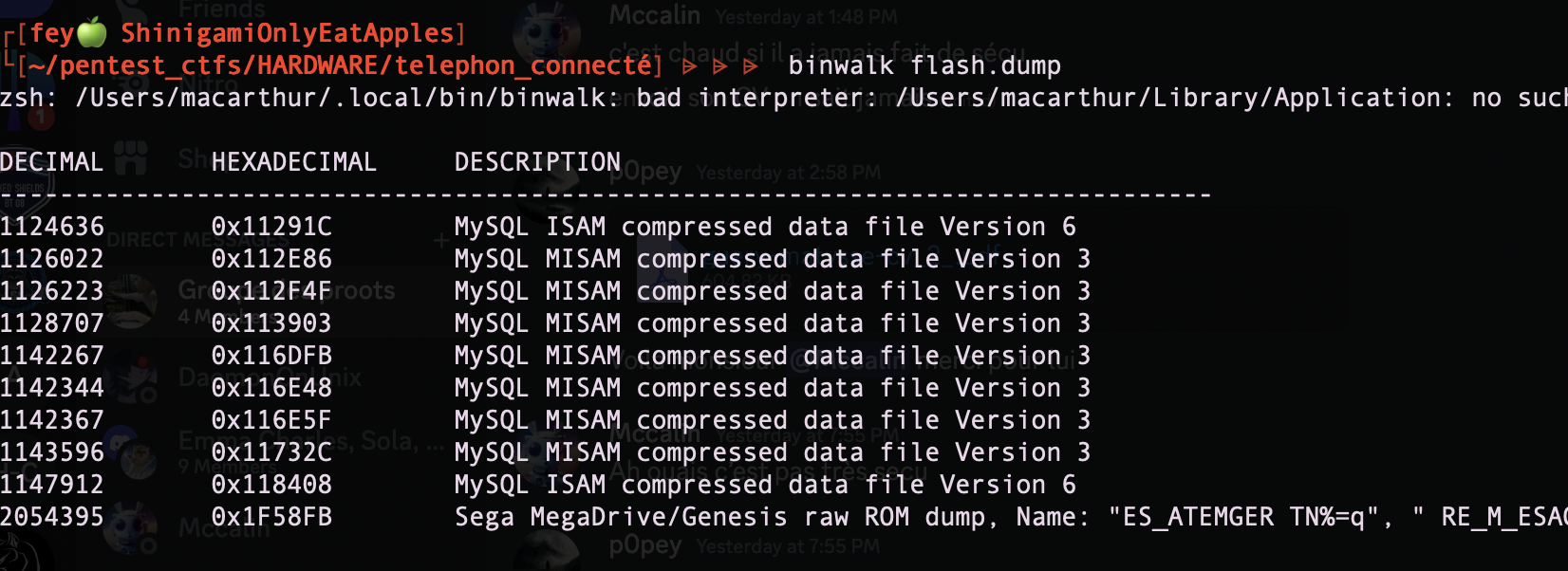
No luck, it seems that there is no obvious Filesystem and moreover all those "MySQL" stuff seems to be only false positive.
At least I can hope that there are some readable data, I can verify that with the simple strings command
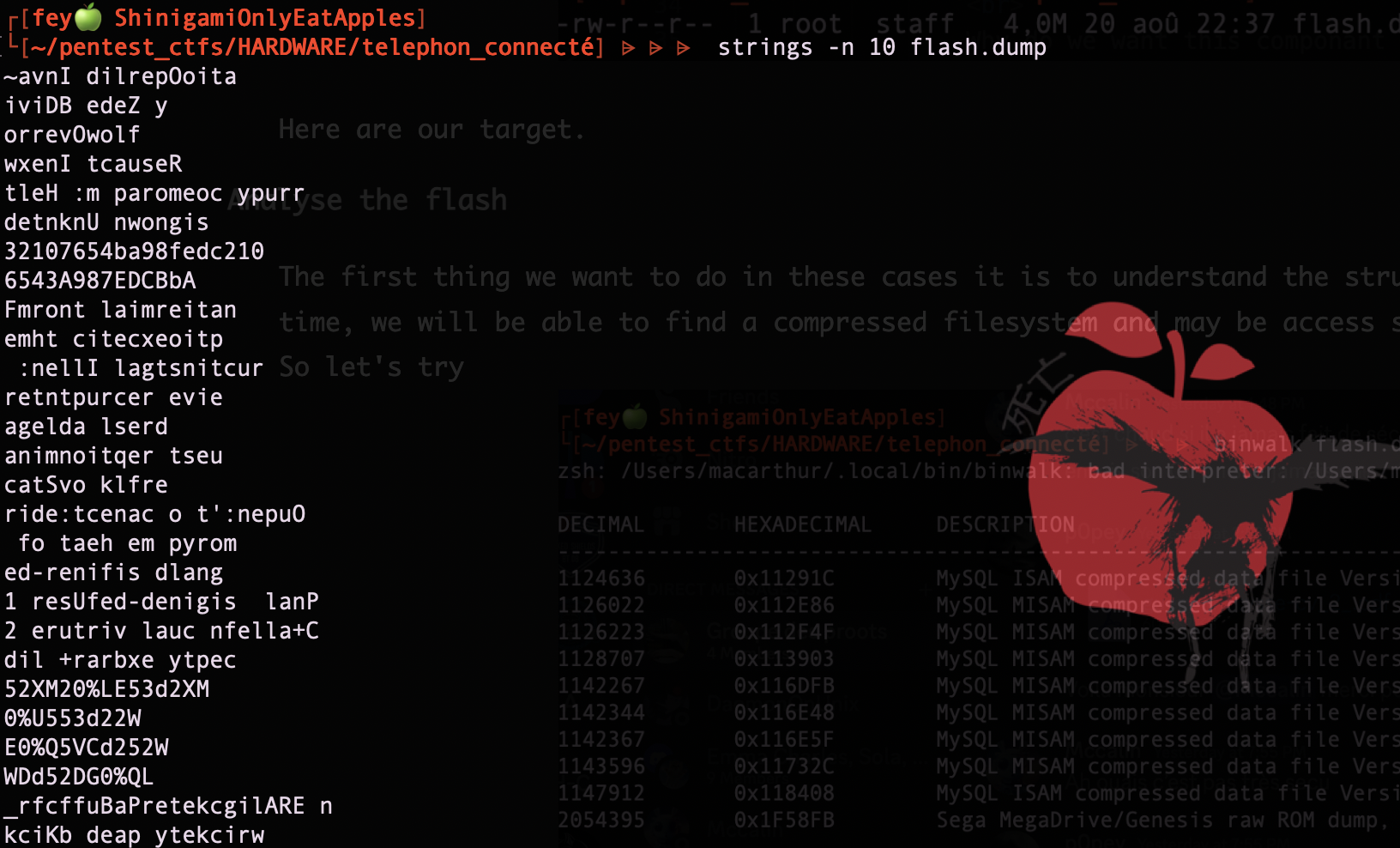
data is readable but weird. If I look closely to the ouput I can find some hints, for example with strings like
... ptthr//: ...
I recognize the http:// pattern but it is just swapped and moreover every 4 bytes, so i figured it is just the endianess that needed to be swapped.
I go to my cyberchef --> #recipe=Swap_endianness('Raw',4,true) and download the result
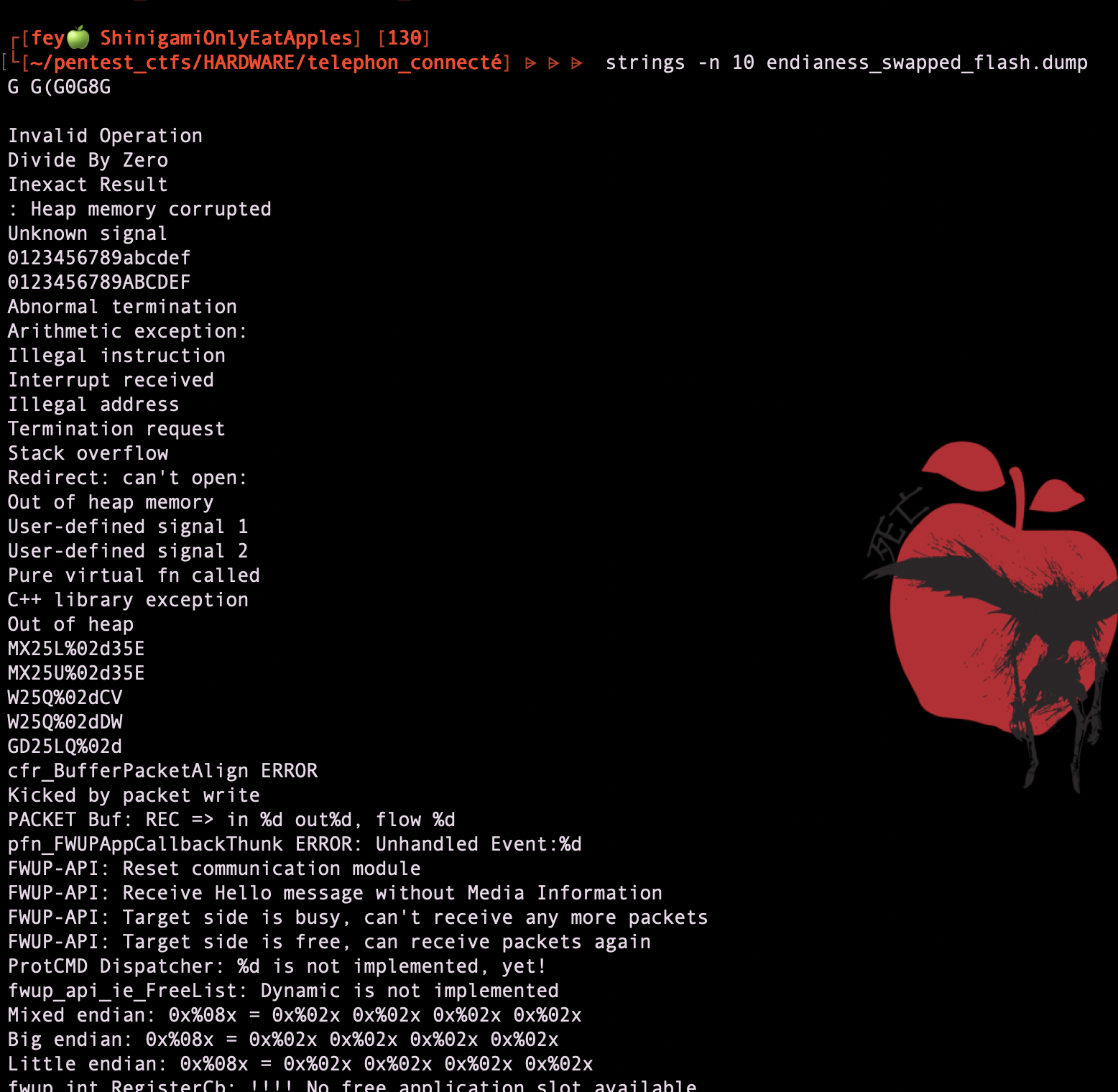
here are some truely readable data by the way, many data are intersting C and low level stuff but let's focus on the one and only the goal, change the logo ! #hacker
Find the initial logo
I ran once again binwalk but it is pretty much the same result as before.
So let's just find the logo by our own.
My idea was, if the image is inside the dump it could be in a simple format such as grayscale or RGB so if I use some python libraries I could play a bit with the dump and try to detect the inital logo.
here is an example of the code I used.
import PIL from PIL import Image import time import sys def myfunc(): rawdata = open(sys.argv[1],"rb").read() # creating image object which is of specific color w = 65 h = 8000 im = PIL.Image.new(mode = "RGB", size = (w, h)) i = 0 for y in range(h): for x in range(w): r = rawdata[i] g = rawdata[i+1] b = rawdata[i+2] im.putpixel((x, y), (r, g, b)) i+=3 # this will show image in any image viewer im.show()
And after playing with indexes, formats, width, etc.. here is a thing that cames out.

It is not very clear, not the right color but I am on the good way.
Let's isolate this part of the dump, to calculate the position I selected the pixels above and Preview gives me the scale in this case 65 x 3644 which I multiply by 3 because each pixel is 3 byte so the address must be something around 710580 == 0xad7b4 for the length I used the same technique, select and calculate the size from the pixels. here is my code
import PIL from PIL import Image import time import sys def myfunc(): rawdata = open(sys.argv[1],"rb").read() i = 710580 size=4680 f = open(sys.argv[2],"wb") f.write(rawdata[i:i+size]) f.close() if __name__ == "__main__": myfunc(0,0)
I now have a smaller data that I can upload to cyberchef that has a module to generate image from raw data. Hopefully, it will gives me the right format of the DATA
And After many tries I finnaly found the right parameters:
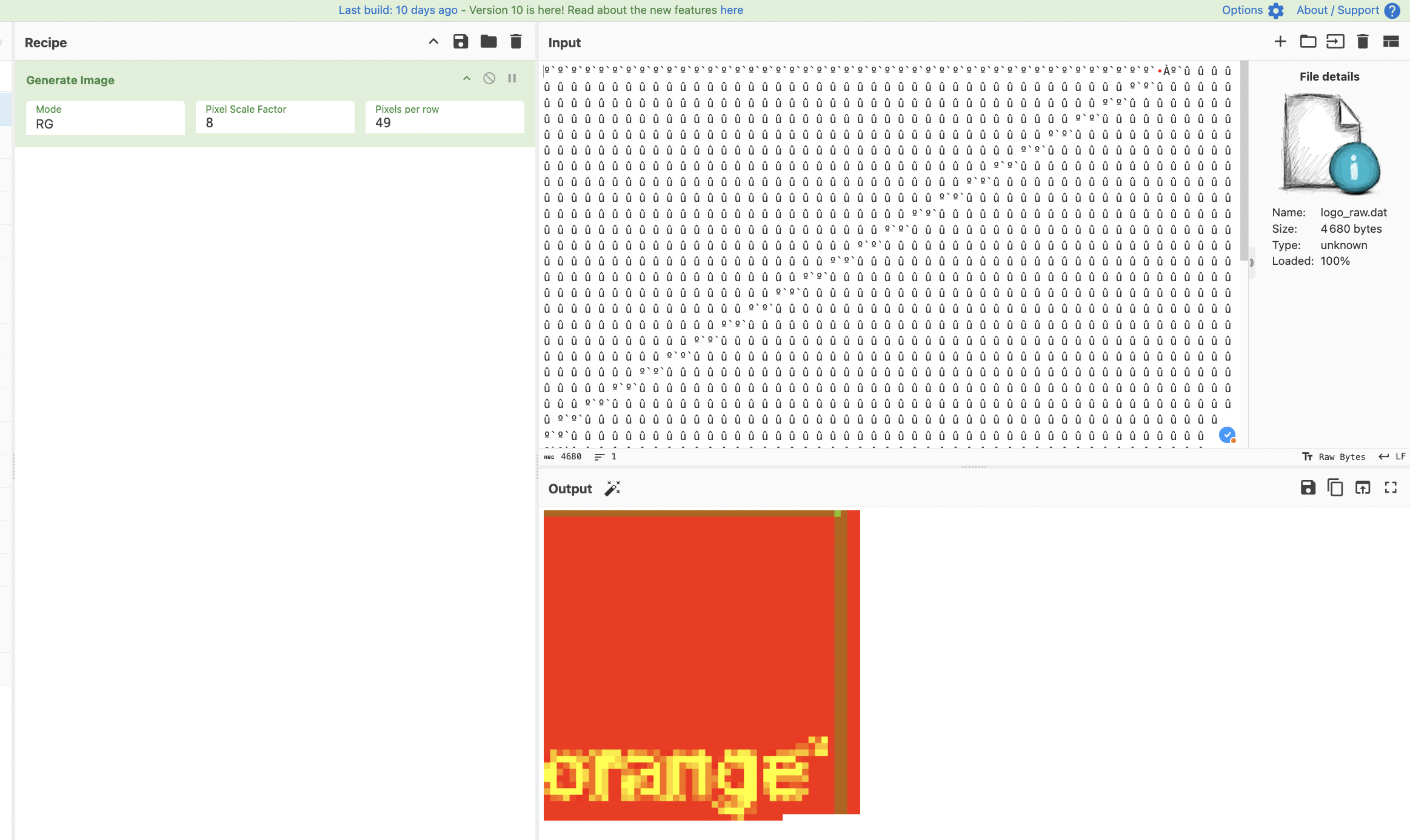
It was a Red Green (only two bytes) format wich is not common .
create a new logo
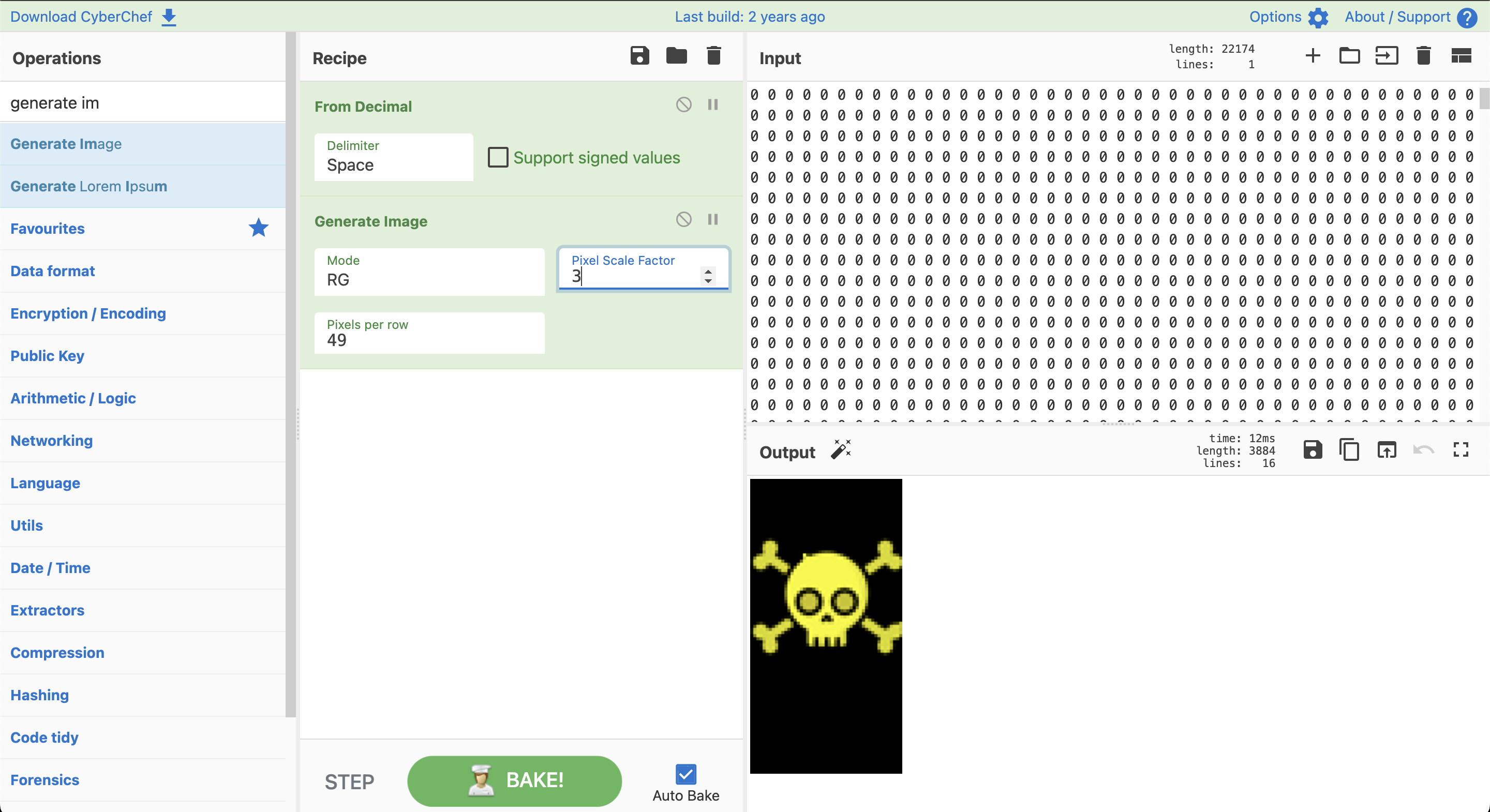
Now that I know the format, let's create a hacker logo in this format, for example let's take this image:
 here is a quick code to retrieve only Red and Green value to fit our format
here is a quick code to retrieve only Red and Green value to fit our format
from PIL import Image # creating a image object im = Image.open(r"/tmp/2699654.png") h = 95 w = 49 for y in range(h): for x in range(w): (r,g,b,a)=im.getpixel((x,y)) print(r,g,end=" ")
then cyberchef to check if the data is OK and then export to raw data
 it is not showed here but actually I removed some 0x00 bytes to reduce the size of the image and try to stick as much as possible to the original logo's size
it is not showed here but actually I removed some 0x00 bytes to reduce the size of the image and try to stick as much as possible to the original logo's size
I do not want to overide data that are not part of the logo :)
it seems valid so I keep going
Replace the data in the dump
Last steps are
1 replace the data inside the memory dump
2 re swap endianess
3 re flash the chip
I use dd the replace the data in the dump "seek=" allows the set the starting index for data writing so has explain earlier we start at 710580
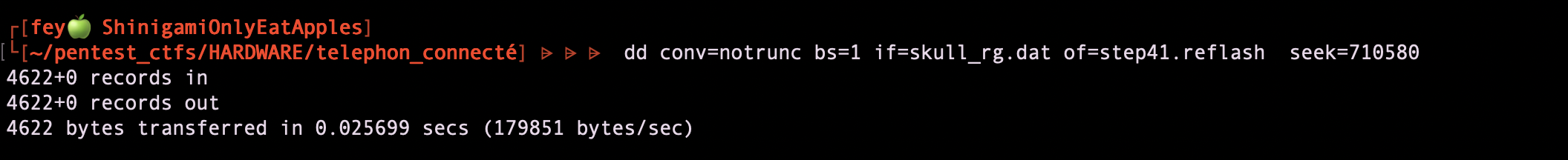
Then I go back to cyberchef to re swap the endianess.
It is time to flash the chip

Final result
Here we go let's boot
 Mission accomplished !
This was quite funny to do, not very usefull I concede but anyway :).
Mission accomplished !
This was quite funny to do, not very usefull I concede but anyway :).

